- Carnivore - Predator
- Formerly known as THC HackSuite, Carnivore - Predator stands at the forefront of cutting-edge cybersecurity tools, redefining the landscape of penetration testing with unparalleled innovation. Designed to empower ethical hackers, security professionals, and enthusiasts alike, Carnivore - Predator is the ultimate Pentest CMS that puts you in command.
THC xExecute Introduction
In this documentation, we will explore the functionality of the thc_xe module.
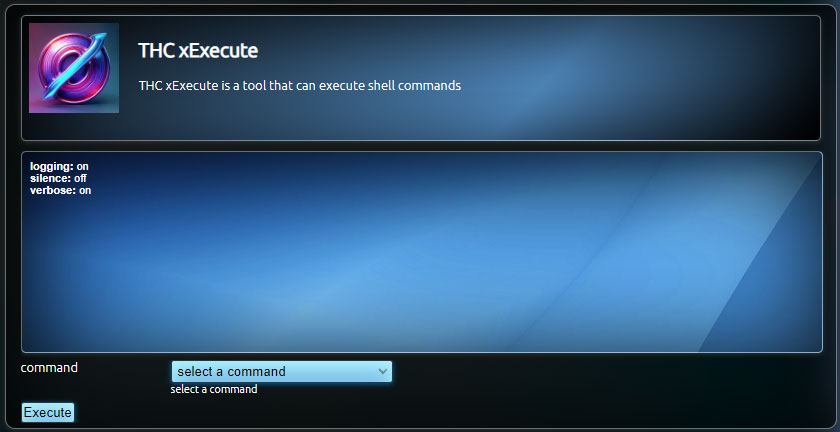
THC xExecute is a tool that allows for safe execution of shell commands in Carnivore, supporting both Linux and Windows platforms.
Interface Parameters:
- Command: The command to be executed.
ModGlue Variables:
- $_CONTEXT['thc_xe']['commandfile']: (string) Absolute path to the commands.php command file in the module's root folder.
- $_CONTEXT['thc_xe']['command']: (array) Command in parts.
- $_CONTEXT['thc_xe']['commanddata']: (array) All data for the command.
- $_CONTEXT['thc_xe']['commands']: (array) All available variations for a command.
- $_CONTEXT['thc_xe']['commandexists']: (boolean) True if the command exists, false if not.
- $_CONTEXT['thc_xe']['commandexecute']: (string) Command to send to the shell after replacing placeholders.
- $_CONTEXT['thc_xe']['commandexecuteoutput']: (string) Print-safe version of the command.
- $_CONTEXT['thc_xe']['commandexecuteraw']: (mixed) False if command failed, string if successful.
- $_CONTEXT['thc_xe']['totaltime']: (int) Total execution time of the command.
Resource Settings:
- Time Limit: PHP default
- Memory Limit: PHP default
Dependencies:
You need to have permission to execute shell commands in PHP.
Expanding THC xExecute:
You can expand THC xExecute's functionality by adding shell commands. Below is an example configuration for a tracert command on Linux:
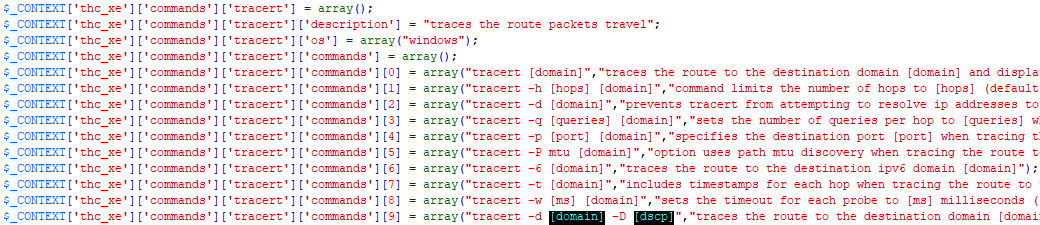
- Description: Describes the command.
- OS: Can be Windows and/or Linux.
- Commands: All variations of the command. In the first part of the array, you can see the command, and the second part provides a description of what task it performs.
In some commands, there are placeholders enclosed in brackets, used as variables and text descriptions for HTML fields, as shown below:
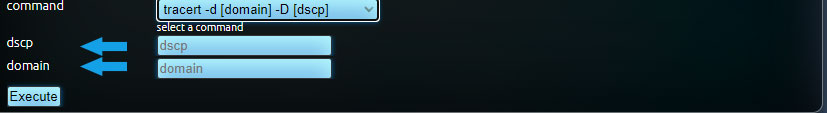
The content within these placeholders must also be validated. Most of the commonly needed placeholders are already validated:
- domain: Validates a parameter that has a domain name pattern value.
- ms: Used for milliseconds validation, but can also be used for numeric values.
- queries: Used for amount of queries validation, but can also be used for numeric values.
- port: Validates a TCP/UDP port number.
- host: Validates a parameter that has a host name pattern value.
- ipv6: Validates IPv6 values.
- ipv4: Validates IPv4 values.
If you want to use other placeholders, ensure they contain no spaces or other special characters. To validate this input, you need to edit the screen.php file in the module's root folder.
Known Issues:
N/A