- Carnivore - Predator
- Formerly known as THC HackSuite, Carnivore - Predator stands at the forefront of cutting-edge cybersecurity tools, redefining the landscape of penetration testing with unparalleled innovation. Designed to empower ethical hackers, security professionals, and enthusiasts alike, Carnivore - Predator is the ultimate Pentest CMS that puts you in command.
THC Inject IT Introduction
In this documentation, we will go through the functionality of the thc_ii module.
THC Inject IT is an automated tool that can inject multiple payloads into the variables inside the query string. One or more targets can be attacked in one session in order to find potential flaws. InjectIt has the capabilities to find SQL injections, local file injections, remote file injections, and XSS.
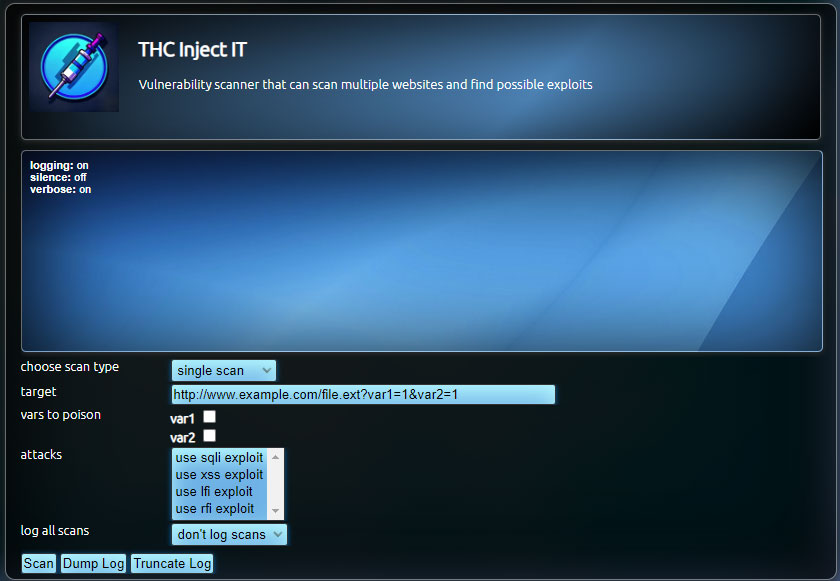
Interface Parameters:
- choose scan type: single scan or mass scan, in case of a mass scan you need to provide a file located in the module folder urls in this file you need to write each url on a separate line
- target: write full URL path and include the query variables, once entered click outside the text field and the vars to poison will be updated
- vars to poison: select the variables you want to poison
- attacks: select all types of attacks you want to perform on the target or targets, you can select multiple types of attacks
- log all scans: in case you want to log scans, the file default.php in the module's log folder is used
ModGlue Variables:
- $_CONTEXT['thc_ii']['log']: (string) path to default log
- $_CONTEXT['thc_ii']['exclude_poison_vars']: (array) variables that won't be poisoned
- $_CONTEXT['thc_ii']['include_poison_vars']: (array) variables that will be poisoned
- $_CONTEXT['thc_ii']['poison_vars_amount']: (int) amount of vars that are poisoned
- $_CONTEXT['thc_ii']['url_text_file']: (string) absolute path to the text file
- $_CONTEXT['thc_ii']['exploits_selected']: (int) amount of exploits selected
- $_CONTEXT['thc_ii']['buffer']: (string) result buffer
- $_CONTEXT['thc_ii']['attack_id']: (string) randomly generated attack id
- $_CONTEXT['thc_ii']['attacks_skipped_buffer']: (string) buffer all attacks that didn't succeed
- $_CONTEXT['thc_ii']['attacks_skipped']: (string) last attack that didn't succeed
- $_CONTEXT['thc_ii']['attack_urls']: (array) data from URL file
- $_CONTEXT['thc_ii']['attack_urls_count']: (int) number of URLs to attack
- $_CONTEXT['thc_ii']['inject']: (array) payload and response patterns from inject.php located in the root folder of the module
- $_CONTEXT['thc_ii']['attack_url']: (string) URL containing payloads
- $_CONTEXT['thc_ii']['response']: (array) response after injection
- $_CONTEXT['thc_ii']['curloptions']: (array) data containing properties for curl connection
- $_CONTEXT['thc_ii']['result']: (boolean) true when the injection was successful, false if not
- $_CONTEXT['thc_ii']['response']['data']: (string) server's HTML output after the injection
- $_CONTEXT['thc_ii']['this_session']: (string) key to identify session
Resource Settings:
- time limit: PHP default
- memory limit: PHP default
Expanding THC Inject IT:
You can expand THC Inject IT's functionality, for example, by adding patterns and responses in the file inject.php located in the root folder of this module.
$_CONTEXT['thc_ii']['inject']['ATTACK_IN_LOWERCASE']['trigger'] = "PAYLOAD";
$_CONTEXT['thc_ii']['inject']['ATTACK_IN_LOWERCASE']['response'] = array("POSSIBLE RESPONSE 1","POSSIBLE RESPONSE 2","...");
ATTACK_IN_LOWERCASE: will create an option in the selection menu
PAYLOAD: single payload, it's not possible to use more than one payload per attack, instead you can make array keys such as xss1, xss2 etc.
POSSIBLE RESPONSE 1: possible responses (not a regular expression pattern, it's a static string), one or more
Dependencies:
- Curl
Known Issues:
THC InjectIT doesn't support _POST requests