- Carnivore - Predator
- Formerly known as THC HackSuite, Carnivore - Predator stands at the forefront of cutting-edge cybersecurity tools, redefining the landscape of penetration testing with unparalleled innovation. Designed to empower ethical hackers, security professionals, and enthusiasts alike, Carnivore - Predator is the ultimate Pentest CMS that puts you in command.
THC AntiEvil Introduction
In this documentation we will go through the functionality of the thc_ae module.
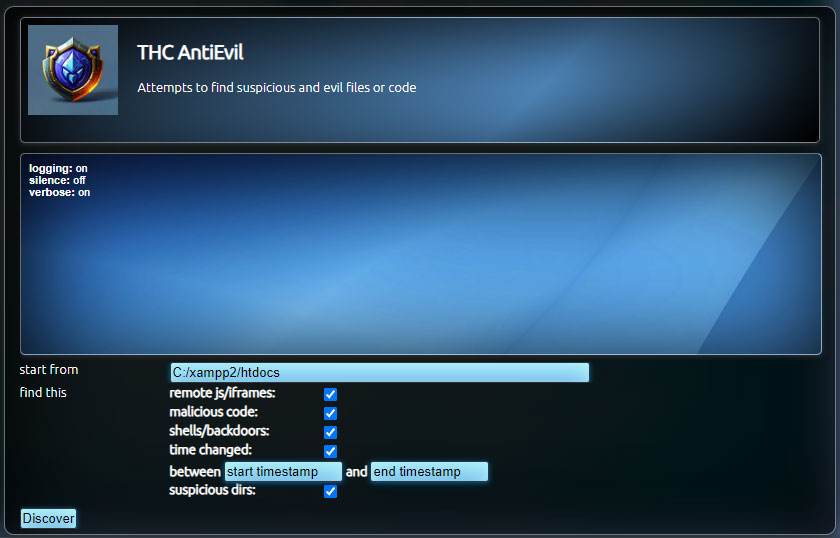
AntiEvil is a useful and configurable tool that can be used to find code that can be potentially harmful to your system. It searches for patterns in source code as well as foldernames and filenames.
Interface Parameters:
- start from: this is the starting point from where the search takes place, the script will search all subfolders and files
- remote js/iframes: searches in scripts for embed, iframe, and script tags
- malicious code: searches for malicious php code
- shells/backdoors: searches for common filenames for shells and backdoors
- time changed: searches files that have been changed between two timestamps
- suspicious dirs: similar to shells/backdoors but searches for folder names
ModGlue Variables:
- $_CONTEXT['thc_ae']['load']: (int) amount of plugins loaded
- $_CONTEXT['thc_ae']['issues']: (int) amount of issues found
- $_CONTEXT['thc_ae']['dirs']: (int) amount of folders browsed
- $_CONTEXT['thc_ae']['files']: (int) amount of files spidered
Resource Settings:
- time limit: 0
- memory limit: php default
Expanding AntiEvil:
You can expand AntiEvil's functionality for example by adding patterns in the data folder or easily add new functionality by creating plugins, if you're an experienced programmer both these processes are straightforward, just read the source.
extra options frontend:
In order to add extra options to the interface, locate the plugins.php file in the root folder of the module where you will find the array $_CONTEXT['thcaeplugs'],these values correspond with the interface fields and a validation file.For example:
$_CONTEXT['thcaeplugs']['iRemote'] = array("remote js/iframes","remote.php");- iRemote: variable name of the input field
- remote js/iframes: text for describing the input field
- remote.php: this is the validation file for the variable $iRemote, you can find these files in the plugins folder in thc_ae
add potential harmful folder names:
Open folders.txt in /data located in the root folder of this module, add new folders on a separate line.
add known backdoor or shell file names:
Open shell.txt in /data located in the root folder of this module, add new files on a separate line.
add patterns indicating potential harmful code:
Open php.txt in /languages located in the root folder of this module, add new files on a separate line. You can add other languages as well, just create a file with the name language.txt and use the same markup as the default file php.txt when you add new items.
AntiEvil also has its own configuration panel, you can find it on this page.
Dependencies:
- N/A
Known Issues:
False positives, it's practically impossible for each scenario to tell whether files are harmful or are part of the functionality.