- Carnivore - Predator
- Formerly known as THC HackSuite, Carnivore - Predator stands at the forefront of cutting-edge cybersecurity tools, redefining the landscape of penetration testing with unparalleled innovation. Designed to empower ethical hackers, security professionals, and enthusiasts alike, Carnivore - Predator is the ultimate Pentest CMS that puts you in command.
current version: 0.7.0 - PREDATOR
This article explains how to effectively make use of HTTPAuth.
author: Remco Kouw
created: 01-May-2024
updated: 01-May-2024
HTTPAuth Introduction
This documentation provides an overview of the HTTPAuth (thc_ht) module functionality.
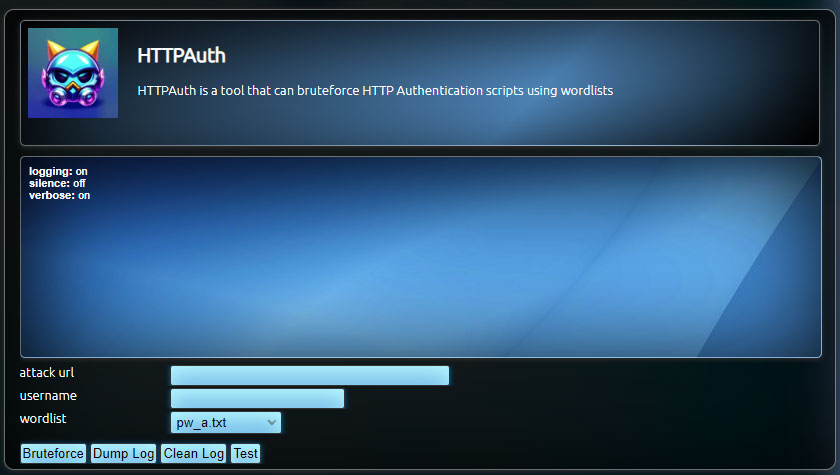
The HTTPAuth module is designed to attack Basic HTTP Authentication scripts using dictionary attacks to gain access.
Interface Parameters:
- Attack URL: The location of the HTTP authentication.
- Username: The username associated with the account.
- Wordlist: Dropdown menu containing wordlists from the Wordlists folder.
ModGlue Variables:
- $_CONTEXT['thc_ht']['log']: (string) Absolute path to the log file located in the module's root folder.
- $_CONTEXT['thc_ht']['username']: (string) Username to attack.
- $_CONTEXT['thc_ht']['scanurl']: (string) URL path to the authentication script.
- $_CONTEXT['thc_ht']['wordlist']: (string) Filename of the wordlist.
- $_CONTEXT['thc_ht']['urlparts']['host']: (string) Host part of the parsed URL function.
- $_CONTEXT['thc_ht']['urlparts']['scheme']: (string) Scheme part of the parsed URL function.
- $_CONTEXT['thc_ht']['urlparts']['path']: (string) Path part of the parsed URL function.
- $_CONTEXT['thc_ht']['wordlistlocation']: (string) Absolute path to the wordlist file located in the Wordlists folder.
- $_CONTEXT['thc_ht']['wordlistdata']: (array) Passwords from the selected wordlist.
- $_CONTEXT['thc_ht']['wordscount']: (int) Number of passwords in the wordlist.
- $_CONTEXT['thc_ht']['keys']: (array) Data from the log file (only applies to the Dump Log case).
- $_CONTEXT['thc_ht']['found']: (boolean) Status of the brute-force process (true if the password was found, false otherwise).
- $_CONTEXT['thc_ht']['request']: (string) Request string for HTTP authentication.
- $_CONTEXT['thc_ht']['attempts']: (int) Total number of attempts.
- $_CONTEXT['thc_ht']['connect']: (resource) cURL connection resource.
- $_CONTEXT['thc_ht']['password']: (string) Password string.
- $_CONTEXT['thc_ht']['response']: (string) Response from the authentication script after sending credentials.
- $_CONTEXT['thc_ht']['totaltime']: (int) Total execution time for the script.
Resource Settings:
- Time Limit: PHP default.
- Memory Limit: PHP default.
Expanding HTTPAuth:
N/A
Dependencies:
cURL
Known Issues:
This module uses dictionary attacks for brute-forcing, which can be resource-intensive. If you encounter time limit or memory issues, consider adjusting the module's settings.
Created by Remco Kouw: 2008-2024