- Carnivore - Predator
- Formerly known as THC HackSuite, Carnivore - Predator stands at the forefront of cutting-edge cybersecurity tools, redefining the landscape of penetration testing with unparalleled innovation. Designed to empower ethical hackers, security professionals, and enthusiasts alike, Carnivore - Predator is the ultimate Pentest CMS that puts you in command.
Medusa Content
Medusa's efficacy is dependent upon the products it supports. Integrating content into Medusa necessitates a foundational understanding of databases, regular expressions, encryption, and open-source software. This document provides a step-by-step guide on how to integrate a new product into Medusa.
As an example, we will utilize the settings for AEF (Advanced Electron Forum). Initially, navigate to the forums directory within the Medusa application.
Each directory contains one or more configuration files for a supported Medusa product. Each file can be accessed in two ways: as an include file or by providing settings to the Medusa GUI via a JSON request.
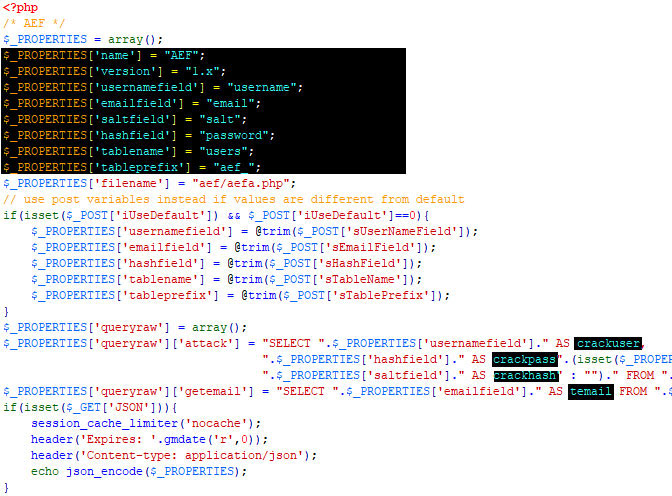
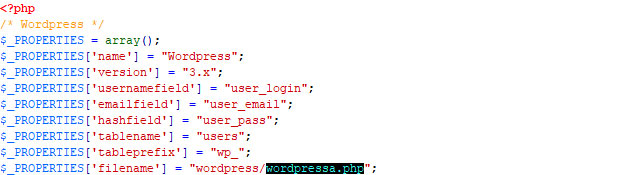
The $_PROPERTIES array encompasses all settings. The default database settings for the product highlighted in the example can be overridden using the Medusa GUI.
- name: Name of the product, which must match the directory name
- version: Supported version
- usernamefield: Database field where the username is stored
- emailfield: Database field where the email is stored
- saltfield: Database field where the salt is stored (leave empty if no salt is used for password encryption)
- hashfield: Database field where the encrypted password is stored
- tablename: Name of the database table where authentication data is stored
- tableprefix: Optional prefix for the product's database tables (leave empty if no prefix is used)
- filename: Relative path to the current file
Subsequently, you will encounter two queries necessary for obtaining the information required to initiate the cracking process. As each product utilizes different names for table fields, aliases are employed when retrieving user data.
- crackuser: Username of the current account
- crackpass: Encrypted password of the current user
- crackhash: Salt used during the encryption process
- temail: Email of the current user
The final section includes an if-statement to check whether this file was accessed from the user interface using a JSON request. If so, this file will provide the necessary settings for this product, and Medusa will populate the form fields within the index's user interface.
The $_SYSTEM array specifies the location of the configuration file for the product and all patterns used to extract the database password, username, host, and name where the product is installed.
These patterns are employed to create a Medusa Shell. This (encrypted) shell is utilized to search for the configuration file (in this instance, the universal.php file), and upon access, it will retrieve those credentials for you.
Authentication Process:
Each product necessitates a unique approach to password cracking. Some products utilize third-party software for encryption, some use salts, and others do not. Therefore, all product authentications are configured manually. These configurations can be found in Medusa's root directory within the crackmeclass.php file, where the class is called THC and has one method of interest.
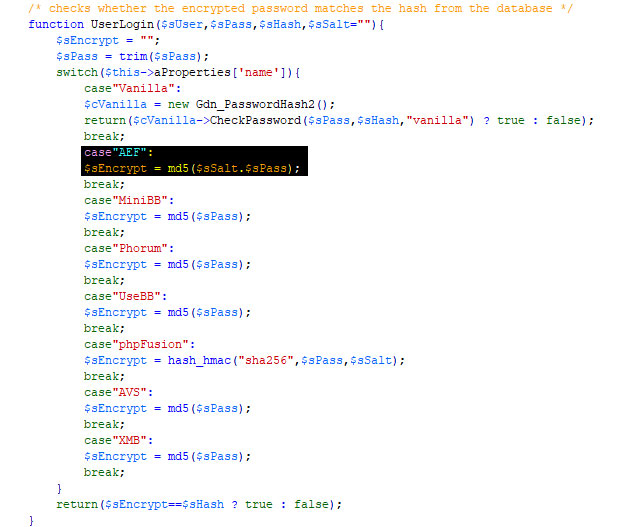
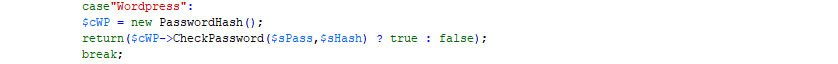
For demonstration purposes, the UserLogin method has been simplified. Each time a new product is added, it must be included here within the switch statement. The case label should always match the name used for the product in the properties file discussed earlier.
The authentication method used depends on the product and whether the functions for password encryption are built into PHP. For instance, sha1 and md5 are native PHP functions.
If third-party classes are used for authentication, additional steps are required. For example, Wordpress uses non-native PHP methods for password encryption. We will examine a different product called Wordpress, which employs phpass to enhance brute-force resistance by adding randomness and increasing computational cost through iteration counts.
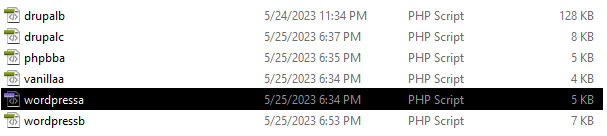
Medusa will check the classes folder in its main directory for a file named after the product in use. In this case, it will look for a file named wordpressa.php that contains the appropriate authentication class or functions.
In the crackmeclass.php file mentioned earlier, there is a line checking whether the password is correct. The result should always be true if the password is correct and false if it is not.
Multiple Versions:
If multiple versions requiring different authentications are present, name the files alphabetically, e.g., producta.php, productb.php, etc. Files for the same product should be located in the same /forums subdirectory.
Medusa Shells:
Medusa Shells are configurable pieces of code that dump the configuration file settings of software. For them to function, these files must be placed in the root directory of the targeted software.
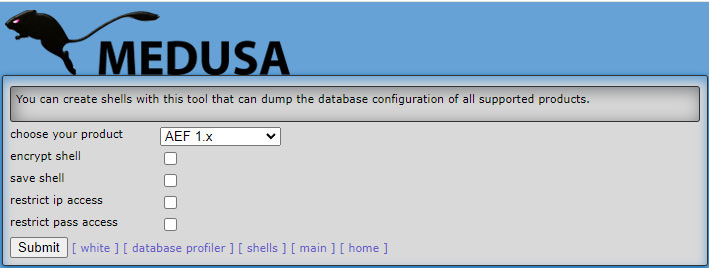
- choose your product: Select the software to target
- encrypt shell: Encrypt the shell to bypass potential WAFs or obscure it from prying eyes
- save shell: Save the shell instead of displaying it as plain text
- restrict ip access: Restrict access to certain IP addresses
- restrict pass access: Restrict access to users with the correct password
All shells are saved in the /Shells directory located in Carnivore's root folder.